What is DNS (Domain Name System)?
Humans cannot remember the IP addresses. That is where DNS (Domain Name System) comes in handy. DNS resolves domain names into IP addresses. DNS holds all the addresses of every device or website that is connected to the internet. It offers a distributed database of website addresses and similar corresponding IP addresses.
DNS is a hierarchical distributed system with authority. It is widespread globally across different servers on the internet. DNS falls under the application layer in the OSI model. DNS support and identify devices that are connected to the internet.
Domain Name System (DNS) servers are the root servers for its domain which contain all the DNS records. TLD (Top-Level Domain) contains a root and ends with .net, .com, and .org. An FQDN (Fully Qualified Domain Name) contains a hostname, domain name, and Top-level domain. For instance – when you are accessing https://www.raghavonsecurity.com – www is the hostname, raghavonsecurity is the domain name, and .com is the TLD (Top-level domain).
How does DNS resolves?
DNS Resolves:
Whenever any webpage is loaded, DNS resolves. DNS must be resolved so the browser can initiate a TCP connection to an HTTP request. The actual DNS resolution starts when the user types a URL on another web browser. At this moment, the browser asks the operating system for a specific web page.

OS Recursive Query to DNS Resolver
Since the operating system running on your computer doesn’t know where “www.raghavonsecurity.com” is, it queries a DNS resolver. OS sends the query to the DNS resolver with a special flat that informs it is a “recursive query”. It means that the resolver must complete recursion and come up with a response either with an IP address or with an error. Here resolver goes through a process called recursion to convert the domain name into the IP address.
Iterative Query to the Root Server
It starts by querying the root DNS server’s IP of “www.raghavonsecurity.com”. This query does not have a recursive flag, so it is an “iterative query, ” meaning the response must be a location of an authoritative name server, error, or address. Here root is represented in the hidden trailing “.” at the end of the domain name. There are a total of 13 root server clusters from A to M. They are operated by 12 different organizations that report to the Internet Assigned Numbers Authority. All the servers are copies of one master server run by IANA.
Root Server Response
These root servers store the locations of all the top-level domains such as – .io, .in, .org, .com, and many newer generic top-level domains. The root does not know the IP info for “www.raghavonsecurity.com” but it knows that .com holds. .com will return with the location of the .com servers. Here root will respond with 13 locations of .com gTLD servers.
DNS Resolver iterative Query to the TLD(Top-Level Domain) Server
Each of the root servers has 4-13 clustered name servers There are mainly two types of TLDs: ccTLDs (country codes) handled by government organizations and gTLDs (generic) handled by a commercial entity. Both entities are responsible for handling and running these servers. Generally, gTLD servers such as – .com, .net, and .edu are controlled by Verisign .gov by gTLDs.
TLD (Top-Level Domain) Server Response
Each TLD server stores a list of all authoritative name servers for each domain in the TLD. For example – each of the 13 .com gTLD servers holds the list of all the name servers for every other single .com domain. gTLD server does not have the IP addresses for google.com but knows the locations of google.com’s name servers. The .com gTLD servers will respond with the list of all target domain NS records.
DNS Resolver Iterative Query to the target domain NS
Here, the DNS resolver queries one of the target name servers for the IP of “www.raghavonsecurity.com”.
Target Domain NS Response
The queried name server knows the IPs and responds with an A or AAAA address record for the IPv4 and IPv6.
DNS Resolver Response to OS
At this point, the resolver has now completed the recursion process and can respond to the end user’s OS with an IP address.
Browser Initate the TCP Handshake
Lastly, the OS holds the target domain’s IP address and provides the IP to the application browser. It initiates the TCP connection to start loading the page.
DNS(Domain Name System) Records
DNS records that remain in authoritative DNS servers provide information about a domain including the associated IP address of the domain and handling of the requests. You can take DNS records like business listing portals. Those portals hold a bunch of useful information such as – locations, services offered, contact numbers, company’s email address, etc. In the same way, DNS holds all such kinds of information in terms of internet information. However, all domains carry at least a few essential DNS records for a user to access their websites by their domain name. Other optional records come with additional purposes.
DNS Records
- A Record – It holds the IPv4 address of a domain.
- AAAA Record – It holds the IPv6 address of a domain
- CNAME Record – It holds one domain to a subdomain
- MX Record – It leads the mail to the email server.
- TXT Record – It enables the administrator to enter text in DNS.
- NS Record – It stores the name server for a DNS entry.
- SOA Record – It holds the admin information of a domain.
- SRV Record – It specifies a port for specific services.
- PTR Record – It offers a domain name in reverse lookups.
Note – For demonstration, we have used NSLOOKUP typically preferred, “NSLOOKUP”, a command line utility used in querying the domain name system of the target domain or IP address. This tool comes installed in Windows. Apart from NSLOOKUP, “DIG” is another command utility usually used In querying the DNS of the domain name or the IP address. For better insights, NSLOOKUP is preferred.
Decrypting DNS Records
A Record
The A indicates “Address” and this is the primary type of DNS record. It indicates the IP address of a given domain. The most common use of A record is IP address lookups. Mainly for matching a domain name for instance raghavonsecurity.com to an IPv4 address. This helps the user to remember the website instead of memorizing the IPv4 address. As explained above DNS resolver automatically carries out by sending a query.
Note – Whenever NSLOOKUP queries the domain name, it returns a non-authoritative answer. Non-authoritative DNS servers are recursive or caching DNS servers. It does not store the primary DNS records for domains. Rather it stores the cached DNS responses.
Copyright reasons hide some domains. You can easily find different domains or your target domain to get the domain name records.
Breaking Down A Record
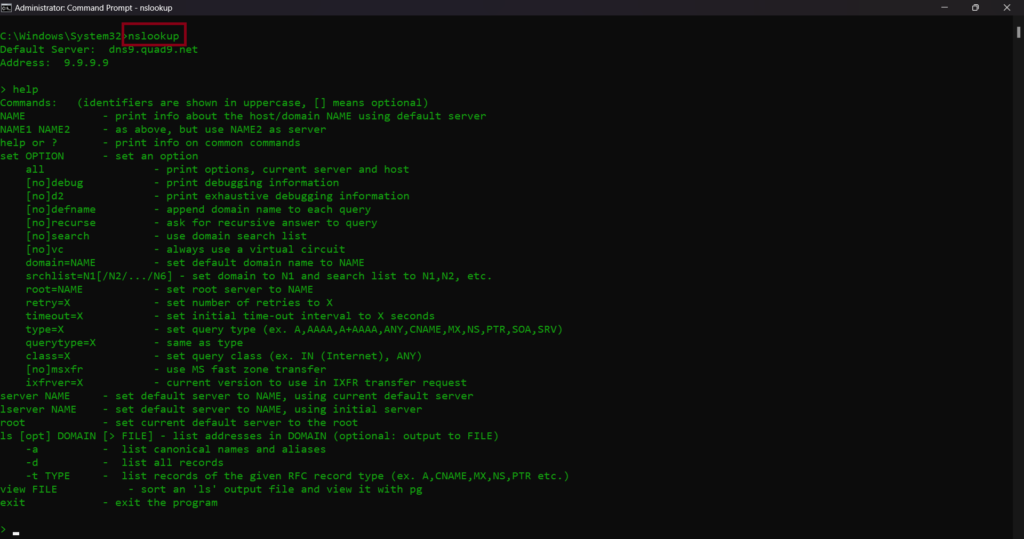
- To query an A record, open CMD. Type below commands
nslookup
set type=a
hackthissite.org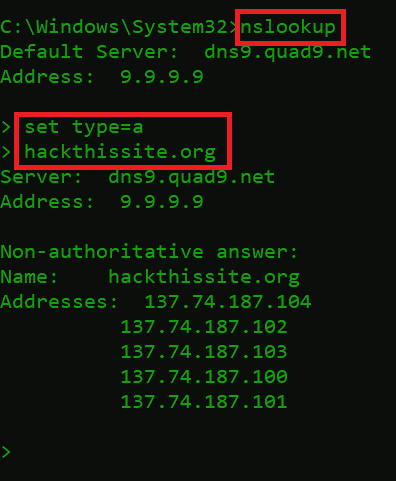
- The above queried DNS record responded with 5 IPv4 addresses – 137.74.187.102. Instead of using a domain name, users can also use an IPv4 address. A record is defined to map an IP address to the domain name.
AAAA Record
An IPv6 address is associated with an AAAA record, which is very similar to an A record. It stores the IPv6 address as the latest version of the Internet Protocol (IP). An IPv6 address is a bit longer than an IPv4 address. IPv6 has more permutations and more possible IP addresses. Like an A record, it recognizes the IP address connected to the domain name.
Breaking Down AAAA Record
- Type below commands
set type=aaaa
hackthissite.org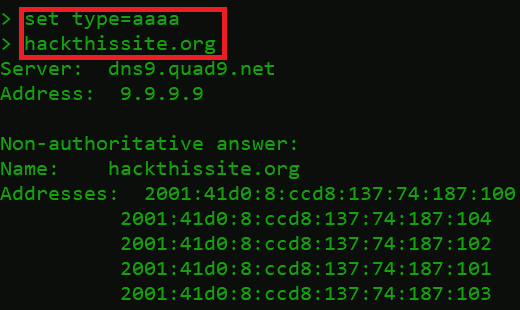
- The above screen responded with the IPv6 address – 2001:41d0:8:ccd8:137:74:187:100. nowadays, IPv6 has become an alternative to the IPv4 address. Multiple IPv4 addresses are diminishing that’s why users are opting for the IPv6 address. Another option for mapping the domain name to the IPv6 address.
CNAME Record
CNAME (Canonical) record is used to alias the same name to a single domain name. All CNAME records must point to the domain name and not to the IP address. Instead of creating different records, create an A record for your domain name (examplee.com) indicating the server IP address, and a CNAME record indicating your domain name (www.examplee.com) indicating to example.com. If the IP address changes, you only have to update A record for your domain name (examplee.com), and (www.examplee.com0 will automatically acquire the changes.
Breaking Down a CNAME Record
- Type below commands
set type=cname
www.raghavonsecurity.com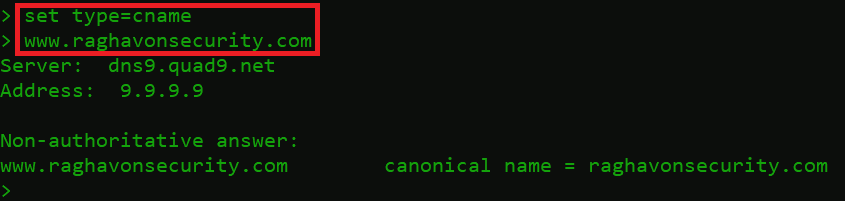
- As we queried www.raghavonsecuriy.com for the CNAME record. raghavonsecurity.com DNS records responded with its canonical domain name.
MX Record
MX (Mail Exchange) record routes email to the mail server. The MX record indicates how emails are routed via SMTP (Simple Mail Trasport Protocol). Whenever someone sends an email to admin@example.com, the MX record will redirect to a specified mail server. MX records prefer multiple email servers, which is a requirement for load balancing and to also avoid outages. MX records are a major part of troubleshooting mail delivery problems.
Breaking Down an MX Record
- Type below commands
set type=mx
hackthissite.org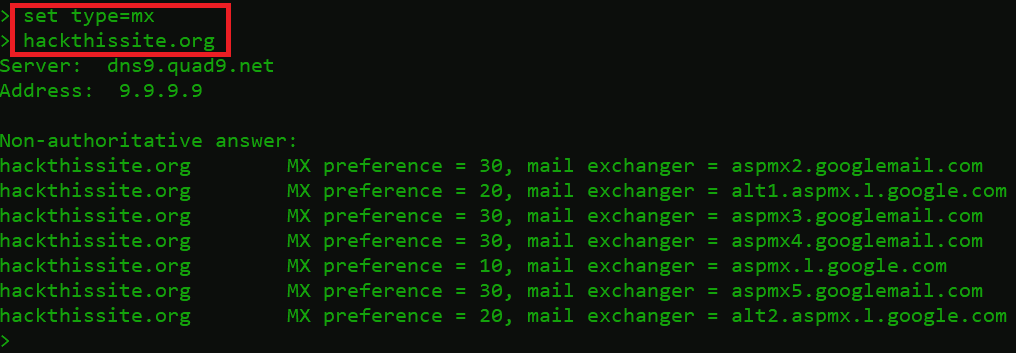
- MX record returned with 7 different mail exchangers.
hackthissite.org MX preference = 10, mail exchanger = aspmx.1.google.com- hackthissite.org – domain name
- MX Preference = 10 – Priority numbers indicate the preference. A lower priority value is always preferred.
- Mail exchanger = aspmx.1.google.com – It’s a specified mail server where the email will be redirected.
TXT Record
TXT (Text) record is used to let a domain administrator enter text in DNS records. It offers the ability to connect text within a zone. These records are used for numerous purposes. One of the common examples is ownership validation. To prove the ownership, a provider needs to require to add a TXT record. However, the main intention of the TXT record is to place human-readable notes. A user can have different TXT records.
Breaking Down a TXT Record
- Type the below commands.
set type=txt
hackthissite.org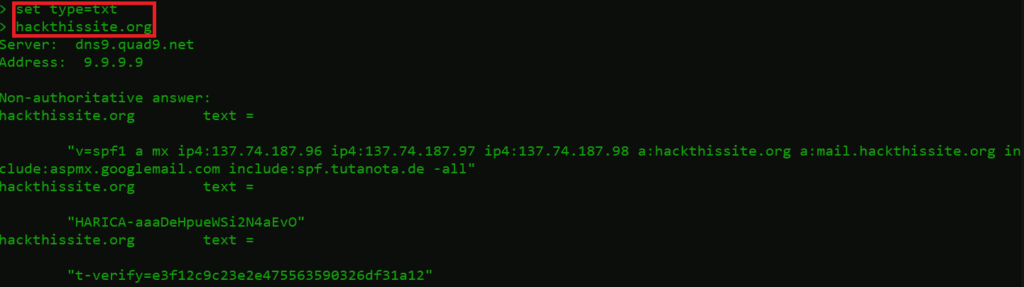
- The above record responded with the 3 txt records:
- “v=spf1 a mx ip4:137.74.187.96 ip4:137.74.187.97 ip4:137.74.187.98 a:hackthissite.org a:mail.hackthissite.org include:aspmx.googlemail.com include:spf.tutanota.de -all” hackthissite.org text – SPF (Sender Policy Framework) records contains a list of IP addresses and the SMTP servers for each IP address. The main motive of SPF is to check the authenticity of incoming emails from the domain owner before they are delivered to recipients. It contains IPv4 addresses, A, and MX records.
- “HARICA-aaaDeHpueWSi2N4aEvO” – It also contains the HARICA info, which means that the domain has also opted for HARICA validation. A trusted third-party entity that engages with all major Root CA programs.
- “t-verify=e3f12c9c23e2e475563590326df31a12” – It’s a Domain Owner Verification txt record. It provides you with a verification code. It contains an ASCII string that contains the text of your DNS txt record.
NS Record
NS (Name Server) record specifies which DNS server is authentic for that domain means which server holds the actual DNS records). It tells the internet where to proceed and locate the domain’s IP address. A domain always has numerous NS records. However, these NS records always indicate the primary and secondary nameservers.
Breaking Down an NS Record
- Type the below commands
set type=ns
hackthissite.org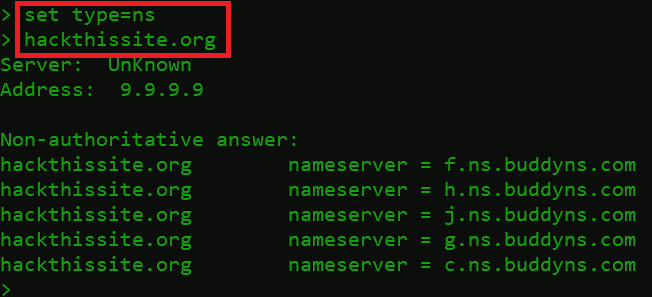
- hackthissite.org DNS NS records responded back with 5 different NS records.
hackthissite.org nameserver = f.ns.buddyns.com- hackthissite.org = domain name
- f.ns.buddyns.com = Hackthissite.org Name server
- These nameservers locate the domain IP address.
SOA Record
SOA (Start of Authority) record stores essential information about a domain such as – the admin email address of the administrator, the domain’s last updation, and the time interval between two refreshes. It includes – firstly, the primary name server of the domain. Secondly, the liable party for the domain. Thirdly, a change in timestamp whenever the domain updates. Fourthly, the number of seconds before the zone refreshes. Fifthly, the number of seconds before a failed refresh is retried. However, the upper limit in seconds before a zone is reviewed as no longer authoritative. Moreover, the negative TTL (i.e. how long a resolver considers a negative result for a subdomain).
Breaking Down SOA Record
- Type the below commands.
set type=soa
hackthissite.org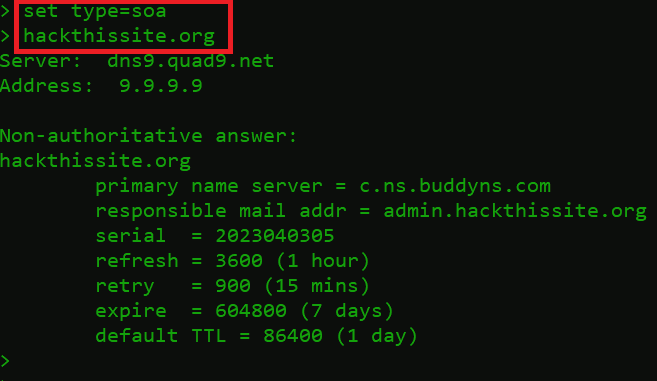
- After querying the SOA record for the hackthissite.org.
- Primary Name Server = c.ns.buddyns.com – is the first point of contact for the web browser.
- Responsible mail addr = admin.hackthissite.org – is the admin email address.
- Serial = 2023040305 – The zone serial number increases when you change the zone file. This helps secondary name servers know when to reload the zone because it’s been updated.
- Refresh = 3600 (1 hour) – This is the time gap, measured in seconds, between update requests sent by secondary and slave name servers.
- Retry = 900 (15 mins) – This is the waiting time, in seconds, that the secondary or slave will pause before trying again if the previous attempt has failed.
- Expire = 604800 (7 days) – This is the waiting time, measured in seconds, that a master or slave server will pause before regarding the data as outdated if it can’t connect to the primary name server.
- Default TTL (Time to Live) = 86400 (1 day) – This is the amount of time, in seconds, that a domain name is already saved on a local device before it expires and the device goes back to the authoritative nameservers to get updated information.
SRV Record
SRV (Service) record defines a host and port for specific services such as VOIP (Voice Over IP), instant messaging, and so on. This record typically shows a symbolic name and the transport protocol used in part of the domain name.
Breaking Down an SRV Record
- Type the below commands.
set type=srv
example.com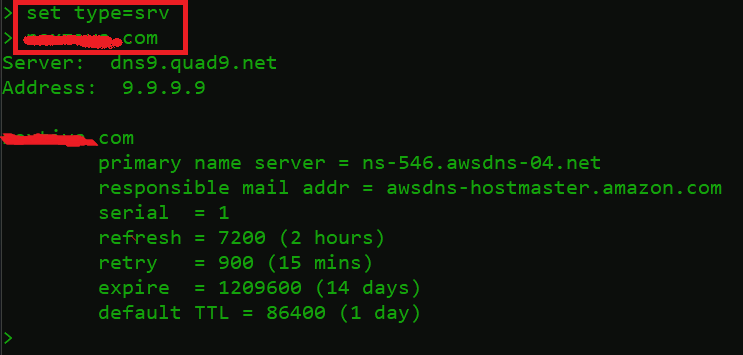
- SRV record returned with: –
- Primary name server = ns-546.awsdns-04.net = It shows the transport protocol with the domain name.
- Responsible mail addr = awsdns-hostmaster.amamzon.com = Another domain name
- Serial = 1 – The zone serial number increases when you change the zone file.
- This tells secondary name servers to reload the zone when it has been updated.
- Refresh = 7200 (2 hours) – This is the time gap, measured in seconds, between update requests sent by secondary and slave name servers.
- Retry = 900 (15 Min) – This is the waiting time, in seconds, that the secondary or slave will pause before trying again if the previous attempt has failed.
- Expire = 1209600 (14 Days) – This is the waiting time, measured in seconds, that a master or slave server will pause before regarding the data as outdated if it can’t connect to the primary name server.
- Default TTL = 86400 (1 day) – This specifies the amount of time, in seconds, that a domain name is saved on a local device before expiring, prompting the device to return to the authoritative nameservers for updated information.
PTR Record
PTR record associates the domain name with IP addresses. The PTR record is exactly the opposite of the A record. This type of DNS record is generally used in reverse DNS lookups. When a user tries to reach a particular IP address. It query initiates with an IP address and looks up the domain name.
Breaking Down PTR Record
- Type below commands
set type=ptr
137.74.187.101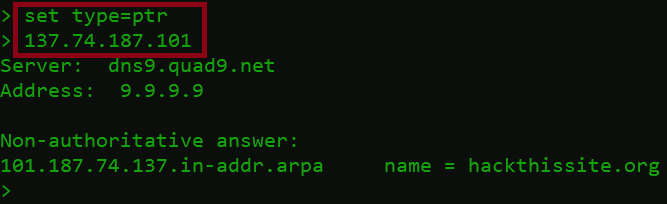
- PTR record responded with:
101.187.74.137. in-addr-arpa name = hackthissite.org- 101.187.74.137. in-addr-arpa = Reverse DNS, rDNS is to determine the domain name associated with an IP address. 137.74.187.101 is the host IP address.
- In in-addr-arpa zone files, it is stored in reverse form as 137.74.187.101 with the dot at the end showing the in-addr-arpa domain.
For more detail understanding, click on the link:
We demonstrate how to use nslookup for DNS querying and troubleshooting. Learn both basic and advanced commands to efficiently resolve domain names. For detailed examples and explanations,
Conclusion
Domain Name System is the unsung hero of the internet, quietly working behind the scenes to make our online experiences seamless. It plays a fundamental role in translating user-friendly domain names into machine-readable IP addresses. The speed and reliability of DNS services are crucial for a smooth online experience, and security measures like DNSSEC help protect against evolving threats.
As we continue to explore new horizons in the digital realm, DNS will adapt and evolve, ensuring that we can always find our way through the vast web of information at our fingertips. Next time you type a web address into your browser, take a moment to appreciate the silent enabler—the Domain Name System—that makes it all possible.
